Networking Settings for Azure Virtual Machine
Originally published on 27 December 2018
While I use key-based ssh(1) to log into my virtual private servers, there are a few steps you can take to harden your servers against the relentless probing and attacks that publicly accessible systems face on the internet. These are by no means an exhaustive list of steps to take but are just a few basic measures I employ whenever I spin up a new virtual machine to provide some additional resiliency.
The configuration file for ssh is located in /etc/ssh/sshd_config for both Linux and BSD systems. Before making any changes, you may want to make a backup copy:
$ sudo cp /etc/ssh/sshd_config /etc/ssh/sshd_config.bak
As you make changes, it's a good idea to refer to the sshd_config(5) man page as it contains a lot of useful information on what the various parameters do.
This should be enabled by default, but if it's not, you can enable it via:
PubkeyAuthenication yesroot LoginVirtually every attacker on the internet will see if they can access your system via the root login. To disable it, set
PermitRootLogin noNote: Be sure that you have created another user account with sudo access that can access your system before you disable root login.
Since I use key-based authentication, there is no need to enter a password to login. Since this is also a common vector by which attackers attempt to gain control of your system, it's a good idea to disable password authentication by setting
PasswordAuthenication noNote: Be sure that you have transferred your public key to the user's ~/.ssh/authorized__keys file before you disable password authentication. To do this, use the ssh-copy-id(1) command:
$ ssh-copy-id -f -t ~/.ssh/id_rsa.pub -p portNumber username@ipAddress
You can then log into that user and double-check that your ssh public key was appended to the ~/.ssh/authorized_keys file.
ssh PortChanging the default port that the ssh daemon listens on does not increase your server's security but does minimize the number of failed login attempts you'll see when evaluating your system's /var/log/auth.log file to see who's trying to access your system. To change the default port that ssh will listen on, update this line:
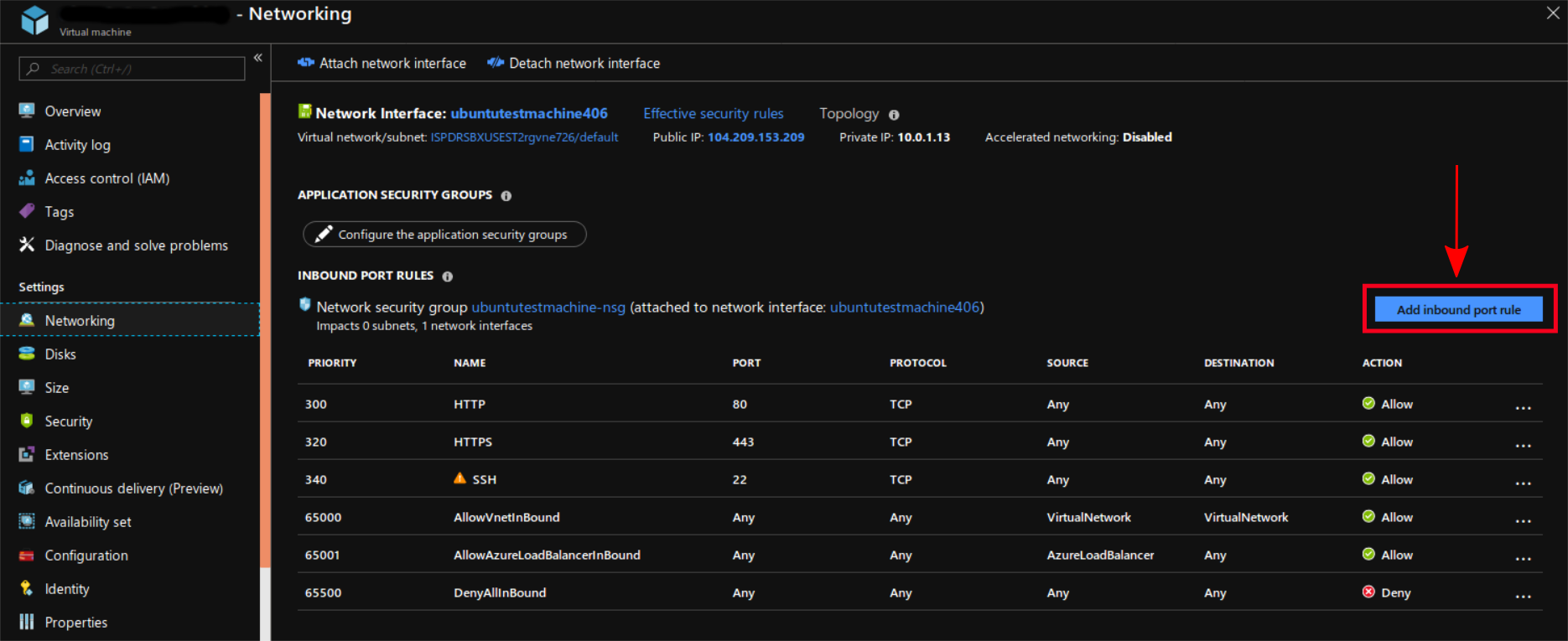
Port XXXXNote: Be sure to update any firewall settings to allow inbound traffic via your new port. You can also block traffic via port 22 if you changed it to another port. Adding a new port on which your system will listen on for SSH traffic is fairly straightforward to do if you have an Azure virtual machine. Within your VM's control panel, click the "Networking" setting and then click the "Add inbound rule" button. See the screenshots below:

Networking Settings for Azure Virtual Machine
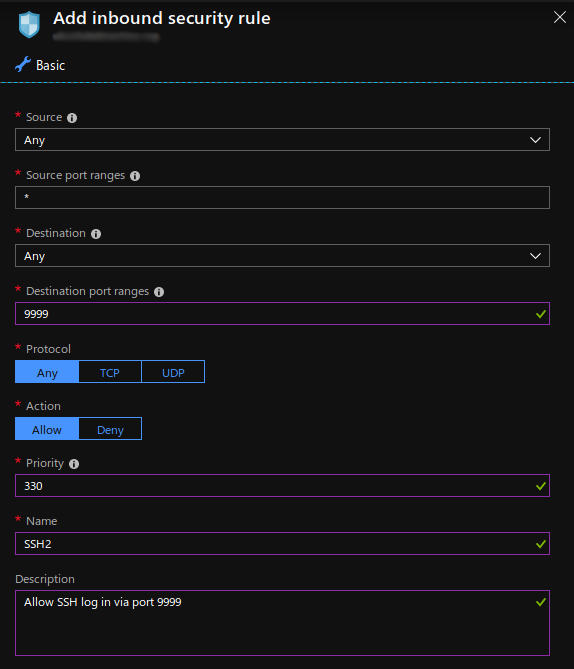
Adding Inbound Security Rule
Changing our server's default ssh port to something other than 22 is a hotly debated tactic with some arguing that this is nothing more than "security by obscurity". By coincidence, there was a good discussion recently regarding this on reddit which is worth reading through.
Note that if you do change the default ssh port that your server listens on to something other than 22, you will have to specify that port number in your client each time you try to log into your server:
$ ssh -p portNumber username@ipAddress
See ssh(1) for more details.
ssh DaemonOnce you make and save your changes to /etc/ssh/sshd_config, you will need to restart the ssh daemon:
$ sudo service sshd restart # freebsd $ sudo service ssh restart # non-systemd linux systems $ sudo systemctl restart ssh # linux with systemd
You should thoroughly test your changes to ensure that they operate in the way you expect. It is a good idea to have a few sessions active when you are making changes. This will allow you to revert the configuration if necessary. Don't log out of your system until you are sure that you can successfully log in using the changes you made.
For additional steps you can take with respect to hardening your system via the various sshd_config settings, please refer to the following links: